Introduction to the AppExchange Security Review : Part 2
Hey, Welcome to another blog on the AppExchange Security Review. If you still haven’t gone through the previous blog on this topic, Please visit the below link: An Introduction to the AppExchange Security Review (Part 1)
Table Of Contents
Before deploying any package or solution to AppExchange, One should ensure that all codes of the package should follow best practices, Moreover one should also remember below points :
Versioning
Submit a point release (ex: 1.4→1.5 etc), not a patch release. Review system is designed to work with major and minor releases but patch releases are not yet supported.
CRUD, FLS
Object (CRUD) and Field Level Security (FLS)can be used to restrict access to sobjects and individual fields. Developers should design their applications to enforce the organization’s CRUD and FLS settings on sobjects, and to gracefully degrade if a user’s access has been restricted. Some use cases where it might be acceptable to bypass CRUD/FLS are: For creating roll up summaries or aggregates that don’t directly expose the data. Make sure to document these use cases as a part of your submission.
Lightning Security — Lightning code shares the same origin as Salesforce-authored code. There are restrictions on third party lightning code, which are enforced by Lightning Locker and a special Content Security Policy. There is also an additional audit for this in the Security Review.
Everything that your package and user interacts with is a target for the Security Review. It’s important that you have to secure every small or big package.Make sure to use Apex Security features like WITH SECURITY_ENFORCED and Security.stripInaccessible , which are now available to use.Always include WITH SHARING or WITHOUT SHARING and always include the latter in False Positives.
Secure Apex Code with User Mode Database Operations – The new Database and Search methods support an access level parameter that lets you run database and search operations in user mode instead of in the default system mode.
Insecure Endpoints
Always use HTTPS when connecting to any external endpoints to push or pull data into Salesforce as a part of your application. Data sent over HTTP is accessible in clear text by any network attacker and poses a threat to the user. Every referenced external web service will be penetration tested, so make sure it’s set up correctly. For more information: Click Here
Common performance issues
Avoid common performance issues such as SOQL queries in nested For loops, DML Statements inside the For Loops, etc.
CSS styling
CSS for LWCs should be in the component’s CSS, not inline. Inline css is strongly discouraged and restricted by the Content Security Model. If your css breaks another component, you’ll fail review.
Note:
Don’t use THIS, fixed, absolute, or float in CSS. Components are intended to be modular and run on pages with others. You can add false positive documentation for this, but it needs to be well justified.
It’s crucial to pay attention to this as CSS may also be used as an attack vector:
- https://css-tricks.com/css-security-vulnerabilities/
- https://www.netsparker.com/blog/web-security/private-data-stolen-exploiting-css-injection/
JavaScript
One thing to consider is to check for legacy versions of libraries, especially jQuery. Legacy versions with known vulnerabilities will cause you to fail review, and is an easy one to resolve ahead of time. Also worth mentioning retire.js again, which can be run as a build task or as a browser extension
Content Security Policy
The Content Security Policy (CSP) Overview is a great resource on how the Lightning Framework uses CSP to impose restrictions on content.The main objective is to help prevent cross-site scripting (XSS) and other code injection attacks. Web browsers follow CSP rules specified in web page headers to block requests to unknown servers for resources including scripts, images, and other data. CSP directives also apply to client-side JavaScript, for example by restricting inline JavaScript in HTML .
JavaScript libraries can only be referenced from an org — All external JavaScript libraries must be uploaded to your org as static resources. The script-src ‘self’ directive requires script source to be called from the same origin. For more information, see Using External JavaScript Libraries.
Resources must be located in your org by default — The font-src, img-src, media-src, frame-src, style-src, and connect-src directives are set to ‘self’. As a result, resources such as fonts, images, videos, frame content, CSS, and scripts must be located in the org by default. You can change the CSP directives to permit access to third-party resources by adding CSP Trusted Sites. For more information, see Create CSP Trusted Sites to Access Third-Party APIs. Even though the resource is located in your org or accessed through a CSP Trusted Site, it must use HTTPS URL for security.
Blob URLs are not allowed in iframes — The frame-src directive disallows the blob: schema. This restriction prevents an attacker from injecting arbitrary content into an iframe in a clickjacking attempt. Use a regular link to a blob URL and open the content in a new tab or window instead of using an iframe.
Cross-site Scripting (XSS)
All standard VisualForce and Lightning components have built-in output encoding to prevent XSS from user-supplied data. XSS vulnerabilities typically arise when output is explicitly disabled.
Ex:
<span style="font-size:16px; background-color:#c2d6f2;"> escape="false" </span>Avoid disabling the XSS protections offered by the platform, and if you must, use the HTMLENCODE or JSENCODE methods to manually apply output encoding. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by your browser and used with that site.
These scripts can even rewrite the content of the HTML page. Stored XSS attacks are persistent and occur as a result of malicious input being stored by the web application and later presented to users.
Code considerations
Commented code — Comments are allowed in small snippets and samples but full functions and classes which are commented out should be removed.
Incomplete test documentation — It’s important that documentation is as complete as possible, including Documenting your responses to false positives. This helps the reviewer understand why something is in a particular way that normally wouldn’t be best practice, and understand what actions you’ve taken to mitigate any security concerns.
Insecure software versions — When new vulnerabilities are discovered in software, it is important to apply patches and update to a version of the software for which the vulnerability is fixed. Attackers can create attacks for disclosed vulnerabilities very quickly, so security patches should be deployed as soon as they are available.
Storing sensitive data —A brilliant resource on how to work securely with sensitive data. If your application copies and stores sensitive data that originated at salesforce.com, you should take extra precaution. Salesforce.com takes threats to data that originated at their site very seriously, and a data breach or loss could ruin your relationship with Salesforce if you are a partner. When storing Salesforce credentials like OAuth access tokens or SSO session information off the platform, make sure to follow industry best practices for secure storage on your development platform. Never store Salesforce passwords off the platform. For external secrets stored on Salesforce, make sure to secure storage mechanisms provided by the platform like protected custom settings, named credentials etc.
Password echo — Storing sensitive information in the source code of your application is rarely a good practice, anyone that has access to the source code can view the secrets in clear text.
Checkmarx Security Scanning With Example
The checkmarx code scanner will check your entire business logic including client side and server-side codes. Based on your code quality, best practice standards, and vulnerability, the issues will be classified.
- Apex Serious Security Risk
- Apex Critical Security Risk
- JavaScript High Risk
- JavaScript Low Visibility
- Apex Code Quality
Following are some of the common AppExchange Solution security threats based on the group type:
- Client DOM (Document Object Model) Stored XSS: JavaScript High Risk
- Multiple forms in Visualforce page
- URL Redirection Attack: Apex Serious Security Risk
- SOQL and SOSL Injection: Apex Critical Security Risk
- DML Statements Inside Loops: Apex Code Quality
Let us discuss these issues along with a solution.
Examples:
1. XSS client DOM stored XSS
DOM-based XSS vulnerabilities mostly occur when JavaScript takes data from an attacker-controllable source. Here, we have added an escape attribute equal to false. Be aware that putting this value to “false” may be a security risk because it allows DOM content, including JavaScript, which could be used in a malicious manner.
<apex:outputText escape=“false” value=“{!Terms_and_conditions__c}”/>
Solution:
<p>{!Terms_and_Conditions__c}</p>OR
<apex:outputText value="{!Terms_and_Conditions__c}" />
2. Multiple forms Issue
- Sample snippet form Visualforce page.
<apex:outputPanel> <apex:form><apex:commandButton value="Custom Action One" action="{!customAction1}"/> </apex:form> </apex:outputPanel> <apex:form > <apex:inputText value="{!customText1}"/><br/> <apex:commandButton value="Custom Action Two" action="{!updateCustomText1}"/> </apex:form> - If you are using multiple forms on the same Visualforce page, we will get “Multiple forms in the same page” issue.
Solution:
- We should have only one form per Visualforce page. Then, add all elements inside that form tag.
3. URL redirection attack
- Do not hard code any URL for redirection. The following format is not a good practice.
String url = hostURL+'/'+salesforce.com/forums/?id=recordId; - If you are returning this string variable for iframe or some other redirection purpose, we will get a URL redirection attack issue.
Solution
- Use page reference class for URL redirection; also you can use EncodingUtil class methods.
String url = hostURL+'/'+salesforce.com/forums/?id= EncodingUtil.urlEncode(recordId, 'UTF8'); PageReference redirect = new PageReference(url); - Visualforce page with iframe redirection to another page.
4. SOQL AND SOSL Injection
- Below is a simple example of Apex and Visualforce code vulnerable to SOQL injection.
VF Page:<apex:page controller="SOQLApexController" > <apex: form> <apex:outputText value="Enter Your Name" /> <apex:inputText value="{!name}" /> <apex:commandButton value="Query" action="{!query}" /> </apex: form> </apex: page>Apex Class (Controller):
public class SOQLApexController { public String name { get { return name;} set { name = value;} } public PageReference query() { String qryString = ‘SELECT Id FROM Contact WHERE ‘ + ‘(IsDeleted = false and Name like \’%’ + name + ‘%\’)’; List queryResult = Database.query(qryString); System.debug(‘query result is ‘ + queryResult); return null; } }
Solution:
- To avoid SOQL injection attacks, do not use dynamic SOQL queries. Instead, use static queries and binding variables for user input and concatenation. The above vulnerable example can be rewritten using the static SOQL as follows:
Apex Class(Controller):public class SOQLApexController { public String name { get { return name;} set { name = value;} } public PageReference query() { String queryName = ‘%’ + name + ‘%’; List queryResult = [SELECT Id FROM Contact WHERE (IsDeleted = false and Name like :queryName)]; System.debug(‘query result is ‘ + queryResult); return null; } }
5. DML Statement inside the for loop
- In your Apex controller or trigger,do not place SOQL or DML statements inside a loop. If you did, database operations will trigger once per iteration of the loop. It will be a reason to reach the SFDC governor limits.
for (Account con : Trigger.New) { Contact con = new Contact (LastName = ‘Test’); Insert con; }
Solution:
- Move all the DML statements outside the loop. If you need to get any data inside the loop to perform DML operations, then use Collections.
list conList = new List (); for (Account acc: Trigger.New) { conList.add(new Contact (FirstName='Info', LastName='Default', Email= 'info@websitedomain.tld', AccountId= acc.Id)); } if(conList.size()>0) { insert conList; } - Here is some more information about the most critical web application security risks and solutions for the same. You can view them at Open Web Application Security Project (OWASP) Top Ten awareness document. (OWASP is a nonprofit foundation that works to improve the security of software)
Sample Report
Sample Report Format without Issue
This is the sample report format you would receive in the email if you triggered a scan for your org. In the image displayed below, you can see the list of queries, issue group (based on risk level), and issue count.
Sample Report Format with Issue
- The following report has 17 issues related to the Lightning API Version, 2 issues regarding FLS Create and 1 for Hardcoding Ids.
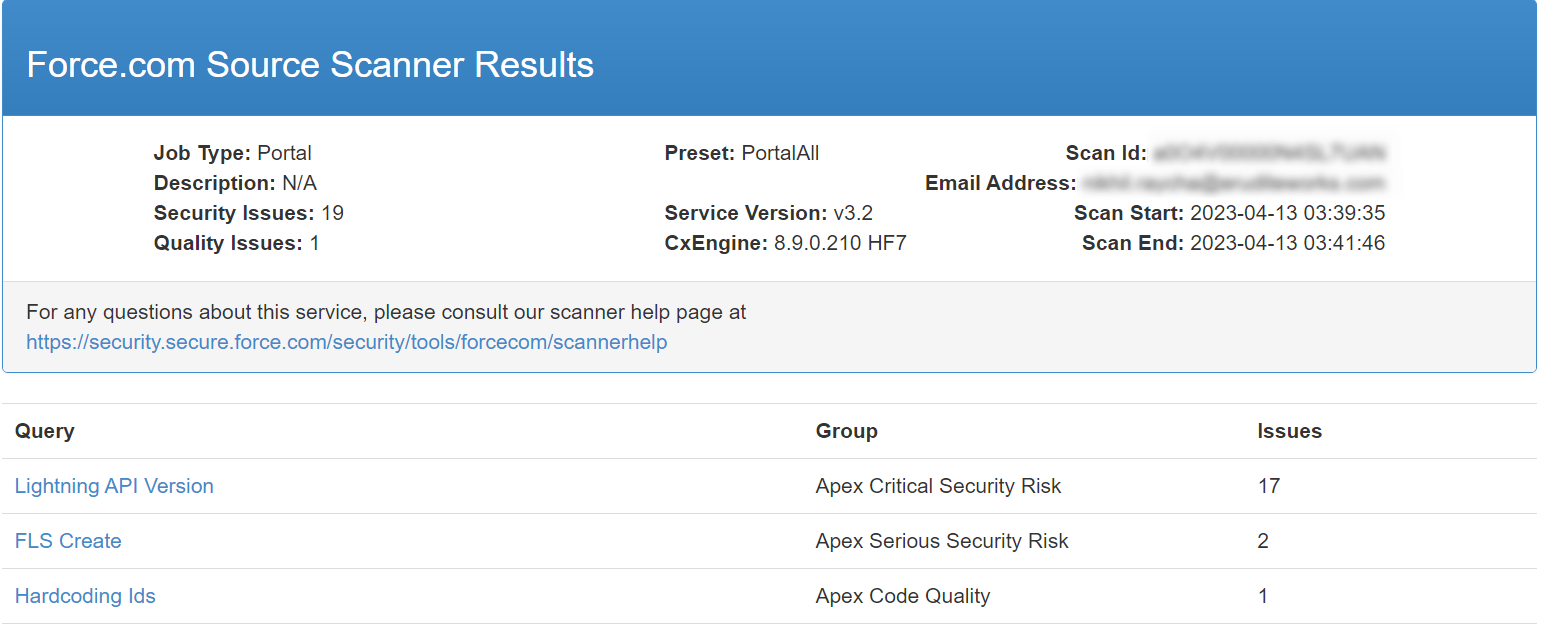
These are the descriptive images, of the Report with issues:
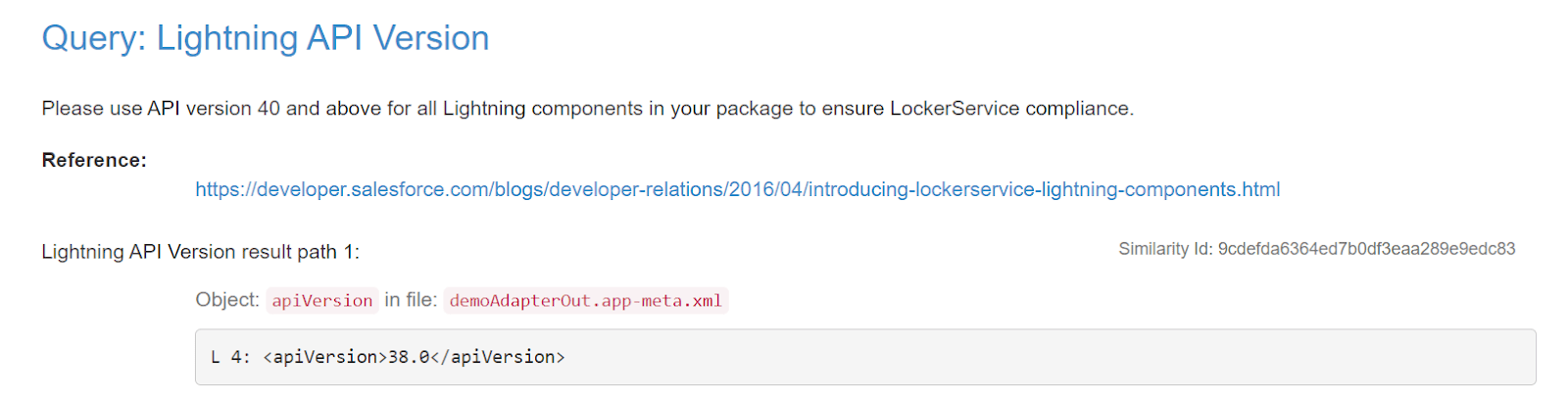
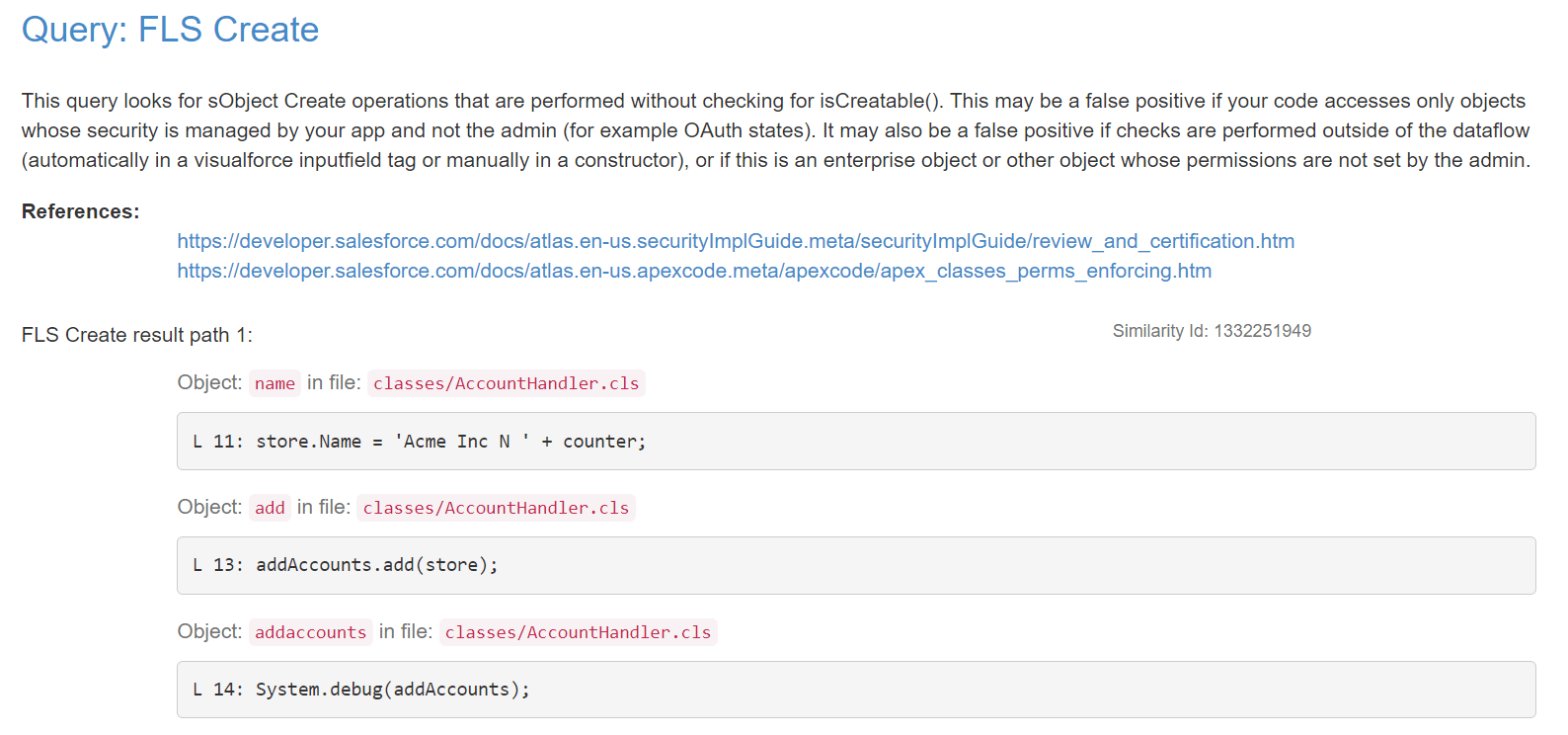
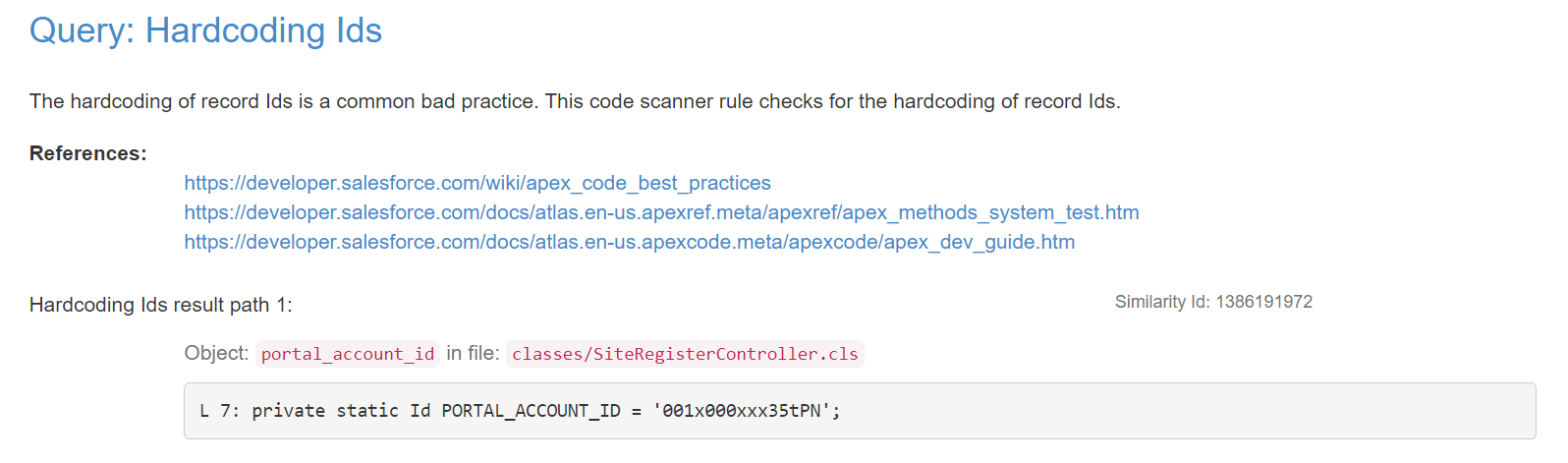
Thank you for checking out our blog! If you’re seeking Salesforce-related services, look no further. Erudite Works is a leading Salesforce consulting firms providing expert strategies, implementation, and customization of Salesforce CRM to optimize your business automation and reporting. Our certified team ensures a seamless CRM solution and exceptional consulting services. Contact Us to learn more about how we can assist your company.






0 Comments
Trackbacks/Pingbacks